Section: Overall Objectives
Context
For verifying the security of infinite-state systems we rely on:
-
different ways to express the safety, reachability or liveness properties of systems, linear-time or branching-time logics, and the application of abstraction or abstract interpretation;
-
the modeling of systems by encoding states as words, terms or trees and by representing infinite sets of states by languages. To each of these structures correspond appropriate action families, such as transductions or rewritings.
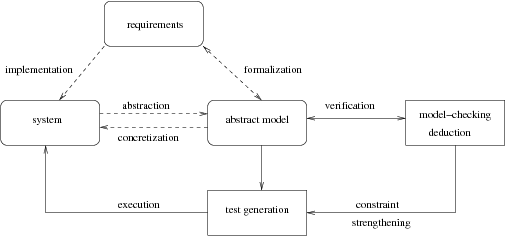
Our goal is to apply these different approaches for ensuring the security of industrial systems by providing adequate methods and tools. In more details we aim at the following contributions (see the continuous lines in Figure 1 ):
-
verification of abstract models derived from existing systems;
-
test generation from the abstract model for validating the existing model;
-
cross-fertilization of the different validation techniques (deduction, model-checking, testing) by taking advantage of the complementary scopes and of their respective algorithmic contributions.
Let us mention that all these techniques comply with various development methodologies.